The 15-Second Trick For Ec2 Backup
Wiki Article
The Ultimate Guide To Aws S3 Backup
Table of ContentsThe Facts About Aws S3 Backup Revealed5 Easy Facts About Aws S3 Backup ExplainedThe Facts About Aws S3 Backup RevealedThe Ultimate Guide To Ec2 BackupSome Known Questions About Rto.Ransomware Protection Things To Know Before You Buy

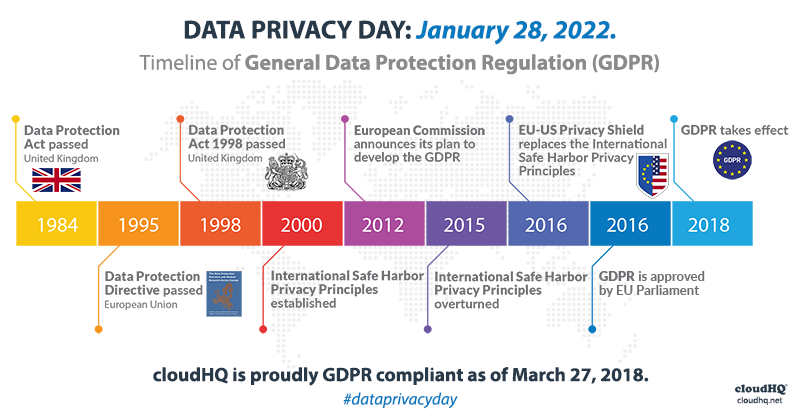
The GDPR highlights the personal information rights of EU locals, consisting of the right to alter, access, remove, or move their data. Individual data refers to any info that relates to a person.
To maintain their data readily available whatsoever times, companies require to keep the IT facilities active also in the situation of a disaster. This state of guaranteed access to data is called data schedule. This short article assesses the fundamentals of information availability and also its challenges, and also provides strategies to maintain a high level of data schedule.
Without an appropriate information safety and security plan, delicate information can drop right into the hands of enemies, enabling them to access to your network, and subject the individual details of customers as well as staff members. This short article presents the concept of data safety and also the various devices and techniques you can make use of to protect your data as well as protect against a disaster.
5 Easy Facts About S3 Cloud Backup Described
Security guarantees the honesty of data by protecting it from unapproved modification. File encryption decreases the threat of accessing data from undependable resources by confirming data's resource.A continual data security system keeps a record of all data adjustments and enables you to bring back a system to any type of previous point. This kind of back-up solves the issue of shedding information developed between two arranged back-ups. It additionally provides protection against assaults like ransomware or malware, along with accidental deletion of data.
Any type of business that processes as well as shops personal data of EU citizens, even if it is not physically located in the EU, need to put on the GDPR regulations. There are 2 main roles in the GDPR: the GDPR Data Processor is an entity that holds or processes this kind of data in support of one more organization, as well as a GDPR Data Controller that gathers or processes personal data for its own functions.
Object Lock protects against things variation removal throughout a user-defined retention period. Immutable S3 objects are safeguarded using object, or bucket-level arrangement of WORM and retention characteristics. This performance offers both data protection, consisting of added security against unintentional or malicious removal along with ransomware and also regulative compliance. Learn more: S3 Item Lock Protecting Data for Ransomware Threats and Conformity The cloud-based membership of Office 365 enables staff members to function anywhere, anytime without the need to host their very own material and e-mails.
8 Simple Techniques For Data Protection
Data security is the process of securing vital information from corruption, compromise or loss. The value of information protection enhances as the amount of data produced as well as saved proceeds to expand at extraordinary prices. There is additionally little resistance for downtime that can make it difficult to accessibility vital details.

The key principles of data defense are to guard and also make offered information under all situations.
The Single Strategy To Use For Rto
Details lifecycle management is an extensive strategy for valuing, cataloging and securing info possessions from application as well as individual mistakes, malware as well as infection assaults, maker failure or facility outages and disruptions. More recently, data management has come to include discovering methods to open organization worth from or else dormant duplicates of data for reporting, test/dev enablement, analytics and other purposes.(CDP) backs up all the data in a venture whenever a modification is made. Data mobility-- the capacity to move information amongst different application programs, computing settings or cloud services-- presents one more collection of troubles and options for information protection.
10 Simple Techniques For Protection Against Ransomware
Information security is the process of protecting essential information from corruption, concession or loss. The relevance of information click to find out more security enhances as the amount of information produced and stored remains to expand at unmatched rates. There is additionally little resistance for downtime that can make it impossible to access vital info (https://sites.google.com/view/clumi0/home).Shielding information from concession as well as ensuring data personal privacy are other vital elements of information protection. The coronavirus pandemic triggered millions of workers to function from home, leading to the need for remote data defense. Businesses need to adapt to ensure they are shielding data wherever staff members are, from a central data facility in the workplace to laptops at house.
The vital principles of data security are to guard and provide information under all situations. The term data defense defines both the operational backup of data in addition to business continuity/disaster recuperation (BCDR). Data protection methods are progressing along 2 lines: data schedule and also information management. Data availability makes sure individuals have the information they require to perform organization even if the data is damaged or shed.
Info lifecycle management is an extensive approach for valuing, cataloging as well as shielding information possessions from application and customer errors, malware and also virus strikes, maker failure or facility outages as well as disruptions. More just recently, information administration has actually come to consist of finding methods to unlock service worth from otherwise inactive duplicates of data for coverage, test/dev enablement, analytics and other objectives.
The Best Strategy To Use For Aws Backup
(CDP) backs up all the information in a business whenever a change is made. Information portability-- the capacity to move data among various application programs, computing settings or cloud services-- provides an additional set of issues and options for data security.Report this wiki page